 Security controls should not be chosen or implemented arbitrarily. They should flow out of an organisation’s risk management process, which begins with defining an overall IT security strategy, then its goals. This should be followed by defining specific control objectives - practical ways the organisation plans to effectively manage this risk. This is where ISO 27001 comes in. Unfortunately, the security controls in operation today typically only address certain aspects of IT or data security, leaving non-IT information assets like paperwork and proprietary knowledge less protected and vulnerable. Sometimes business continuity planning and physical security might be managed independently of IT or information security, whilst Human Resources practices may not recognise the need to define and assign information security roles and responsibilities throughout the organisation. The ISO 27001 standard was introduced to address these issues. The basic bones of ISO 27001 requires that you:
Yes, there is a lot of detail around the standard, but its essence is actually as simple as this. What you’ll be doing when implementing ISO 27001 There are a series of core requirements in the standard, then the actual controls are detailed in an annex at the back of the standard, called Annex A. The idea with these controls is that you choose to implement them subject to the risk assessments and risk treatment work that you’ll have done in the first part of the standard. So one of the fundamental core requirements in the main body of ISO 27001 is to identify, assess, evaluate and treat information security risks. Doing this risk management process will help determine which of the ISO 27001 Annex A controls may need to be applied in the management of those security-oriented risks:
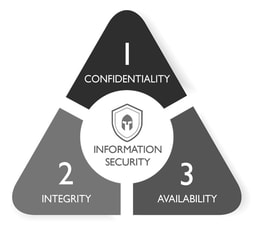
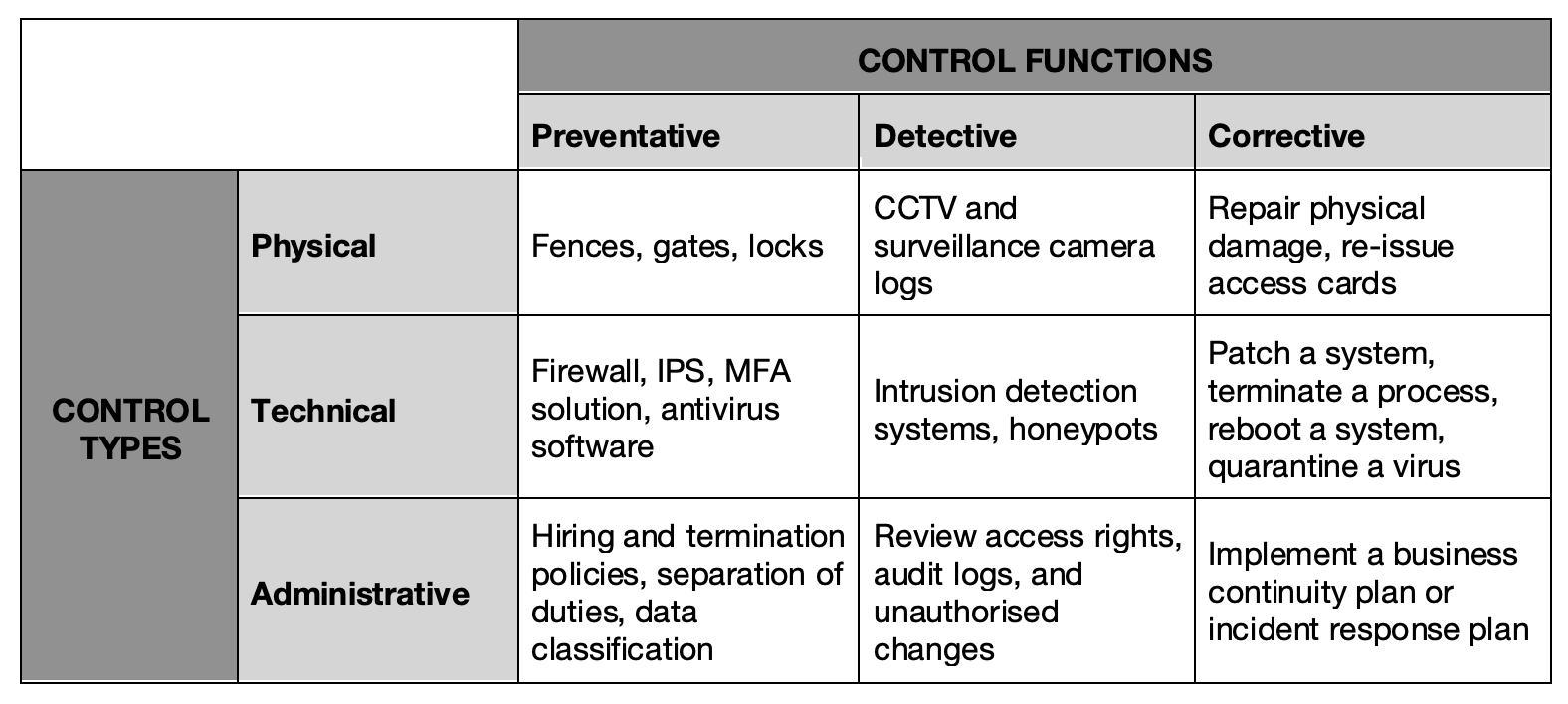
One of the easiest and most straightforward models for classifying controls is by type: physical, technical, or administrative; and by function: preventative, detective, and corrective. Control Types Physical controls describe anything tangible that’s used to prevent or detect unauthorised access to physical areas, systems, or assets. This includes things like fences, gates, guards, security badges and access cards, biometric access controls, security lighting, CCTV, surveillance cameras, motion sensors, fire suppression, as well as environmental controls like HVAC and humidity controls. Technical controls (also known as logical controls) include hardware or software mechanisms used to protect assets. Some common examples are authentication solutions, firewalls, antivirus software, intrusion detection systems (IDSs), intrusion protection systems (IPSs), constrained interfaces, as well as access control lists (ACLs) and encryption measures. Administrative controls refer to policies, procedures, or guidelines that define personnel or business practices in accordance with the organisation’s security goals. These can apply to employee hiring and termination, equipment and internet usage, physical access to facilities, separation of duties, data classification, and auditing. Security awareness training for employees also falls under the umbrella of administrative controls. Control Functions Preventative controls describe any security measure that’s designed to stop unwanted or unauthorised activity from occurring. Examples include physical controls such as fences, locks, and alarm systems; technical controls such as antivirus software, firewalls, and IPSs; and administrative controls like separation of duties, data classification, and auditing. Detective controls describe any security measure taken or solution that’s implemented to detect and alert to unwanted or unauthorised activity in progress or after it has occurred. Physical examples include alarms or notifications from physical sensor (door alarms, fire alarms) that alert guards, police, or system administrators. Honeypots and IDSs are examples of technical detective controls. Corrective controls include any measures taken to repair damage or restore resources and capabilities to their prior state following an unauthorised or unwanted activity. Examples of technical corrective controls include patching a system, quarantining a virus, terminating a process, or rebooting a system. Putting an incident response plan into action is an example of an administrative corrective control. The table below shows how just a few of the examples mentioned above would be classified by control type and control function: The idea is that you implement a combination of security controls based on stated control objectives tailored to your organisation’s needs and regulatory requirements. Ultimately, the goal of both control objectives and controls is to uphold the three foundational principles of security: confidentiality, integrity, and availability - also known as the ‘CIA Triad’.
This Triad of confidentiality, integrity and availability is considered the core underpinning of information security. Every security control and every security vulnerability can be viewed in light of one or more of these key concepts. For a security programme to be considered comprehensive and complete, it must adequately address the entire CIA Triad. Put simply, confidentiality means that data, objects and resources are protected from unauthorised viewing and other access. Integrity means that data is protected from unauthorised changes to ensure that it is reliable and correct. Availability means that authorised users have access to the systems and the resources they need when they need them - there’s no point in having a system so secure that the people who need the information can’t get at it. If you would like to look at how to implement an ISO 27001 information security management system, then simply contact us. Or, if you want to see what's involved in more detail, then get a completely free, no obligation, totally tailored ISO Gap Analysis for your business (only available to UK businesses).
0 Comments
 ISO 27001 is an information security standard, part of the ISO 27000 family of standards, of which the last version was published in 2013, with a few minor updates since then. The family of standards is vast (39 at time of writing), but, as with the other standards, our main focus is on the requirements of ISO 27001. ISO grew out of the British Standard BS 7799 originally published in 1995, having been written by the old Department of Trade and Industry (DTI), and consisted of several parts. The first part contained best practices for information security management, and the second part focused on how to implement an Information security management system (ISMS). Part 3 covered risk analysis and management. Each part became adopted separately at different times by ISO (Part 1 in the year 2000, Parts 2 and 3 in 2005), but since the last review of the standard in 2013 very little reference or use is now made to any of the BS standards in connection with ISO 27001. A quick note about one quirk with this standard - you may see reference to either ISO 27001:2013 or ISO 27001:2017 (note the change in year designation). The 2017 change was introduced to indicate approval by CEN/CENELEC for the EN designation (‘European Standard’), the background to which I’m not going to bore you with here. Needless to say, in practical terms, nothing has changed between the 2013 and 2017 versions of the ISO 27001 standard except for a few minor cosmetic points and a small name change. Either version of the standard is perfectly acceptable and certification can be against either one, it makes no difference. Why get an Information Security Management System? Information is the lifeblood of any business – this is especially true if your clients have entrusted their valuable data to you. Maintaining an Information Security Management System (ISMS) is the most effective way of reducing the risk of suffering a data breach. An ISMS is a systematic approach to managing the security of sensitive information and is designed to identify, manage and reduce the range of threats to which your information is regularly subjected. There are a whole host of benefits to putting in an ISO 27001 management system, such as:
The majority of organisations will generally have a range of different information security controls in place. However, without a formal ISMS these controls tend to be somewhat disorganised, haphazard and disjointed. The reason for this is that the controls have often been implemented over a number of years to firefight specific solutions for specific problems. For example, you used one IT company to put up a firewall but get your antivirus software from an online subscription; you use access cards, but it’s only in the last few years you’ve started collecting them from people leaving the company; you’ve started issuing guidelines to new starters that define business practices applying to employee equipment and internet usage, but don’t know if it’s been issued to employees who’ve been with you for a while now. If you would like to look at how to implement an ISO 27001 quality management system, then simply contact us. Or, if you want to see what's involved in more detail, then get a completely free, no obligation, totally tailored ISO Gap Analysis for your business (only available to UK businesses).  Millions of people around the world have lost their jobs amid the current Covid-19 crisis - it is a crisis within a crisis. The long-term economic impact is yet unknown but will surely be deep. What is not in doubt is that the economic strain on companies of all sizes across the UK and the rest of the world will be here for the foreseeable future. Manufacturers have closed plants, stores are shut, and consumer demand has collapsed in many sectors. Research by the Institute for Social and Economic Research at the University of Essex has found that more than 6.5 million jobs could be lost due to the economic fallout from the UK’s coronavirus lockdown, about a quarter of the UK’s total jobs. A simply staggering number of companies have plunged into administration, from stalwart high street brands to major travel agents, as well as a whole raft of businesses in sectors such as construction. The true toll is only just beginning to be understood. So it’s no surprise that companies which are still managing to keep their heads above water will be starting to look at deep cost-cutting measures in the short- and medium-term. With profit centres being hit like never before, cost centres such as ISO compliance will undoubtedly have fewer resources until the economy turns around. What does this mean for the ISO compliance functions of companies that are struggling? In practical terms, they will have to make risk-based decisions about how to allocate the limited resources that they have. And one important thing to think about is how you can use the expertise of companies such as The Ideas Distillery to outsource your compliance tasks cost-effectively with little overhead. Certification Bodies have recognised, for the moment at least, that the world has changed significantly. Just about all have turned to ‘remote auditing’ as a way to still service clients while still respecting the lockdown. There has also been the option of postponing for up to six months in many circumstances, although this option is now starting to wind down. Any company’s priority will simply be to put themselves in a position to survive the crisis. So when dealing with budget constraints and limited compliance resources, flexibility and creativity will be key. For our part, when we are helping businesses in these scenarios, we always assess risk and conduct a review with the aim of identifying core ISO compliance requirements. This often entails a historic review of internal procedures and controls to identify past activities or other problems to determine where the biggest risks reside. External industry risks such as enforcement actions brought against competitors should be considered as well, along with identifying low-risk areas where there have been few incidents or problems. But more significantly, we help companies to determine if new, immediate significant risks have arisen due to the pandemic. Another emerging risk may exist in a company’s sales department, for example, perhaps due to the pressures of bringing in new business. This may be an area that leads to an increase in customer complaints as things are missed. The crisis may have caused companies to find new suppliers that have not been fully vetted due to time pressures. Likewise, the pandemic may have caused substantial risks to employee safety associated with reopening businesses. This emerging risk will likely call for the development of new policies and procedures that will require close oversight by senior management. For more information - and to see how we can help - just get in touch with us in any number of ways using on our Contact page. If you would like to look at how to implement an ISO 9001 quality management system, then simply contact us. Or, if you want to see what's involved in more detail, then get a completely free, no obligation, totally tailored ISO Gap Analysis for your business (only available to UK businesses). Achieving certification to ISO 27001 demonstrates that your company is following information security best practice, and delivers an independent, expert assessment of whether the data you are handling is adequately protected. Information is the lifeblood of any business – this is especially true if your clients have entrusted their valuable data to you. Maintaining an information security management system (ISMS) is the most effective way of reducing the risk of suffering a data breach. An ISMS is a systematic approach to managing the security of sensitive information and is designed to identify, manage and reduce the range of threats to which your information is regularly subjected. There are a whole host of benefits to getting ISO 27001, such as demonstrating credibility when tendering for contracts, showing you are taking cyber security threats seriously, and avoiding fines and penalties. We identify the key requirements of ISO 27001 for you and provide a top level route map for a successful ISMS implementation in your organisation. We will outline a structured approach to implementation based around:
If you would like to look at how to implement an ISO 27001 information security management system, then simply contact us. Or, if you want to see what's involved in more detail, then get a completely free, no obligation, totally tailored ISO Gap Analysis for your business (only available to UK businesses). |
WelcomeHere you'll find the latest blog articles on all things compliance, particularly focussed on quality, environment, health & safety and information security. Get a completely free, no obligation, totally tailored ISO Gap Analysis for your business...
Categories
All
Archives
April 2024
|
|
Read about our ISO implementation services...
|
Read about our ISO maintenance services...
|

 RSS Feed
RSS Feed


